Fraud Protection
Your Security Is Our Priority
We understand that in today's digital age, fraud can happen to anyone. We are committed to safeguarding your financial information and helping you stay protected against fraud. Here you'll find useful tips, tools, and resources to help you recognize, prevent, and respond to fraudulent activities.
How We Protect You
Fraud Monitoring
Our advanced fraud detection system constantly monitors your transactions for any unusual activity. If we spot something out of the ordinary, we'll alert you immediately, so you can take action quickly.
Real-Time Alerts
Stay in the know with instant notifications about your account activity. Receive text or email alerts whenever there's a large purchase, a new login, or other potentially suspicious behavior.
Multi-Factor Authentication
We utilize state-of-the-art encryption, multi-factor authentication (MFA), and secure login methods to protect your personal information and prevent unauthorized access.
Control Your Cards on Your Terms
Our CardProtect tool allows you to control and monitor your debit and credit cards, giving you the ability to turn your cards on/off at your discretion, add alerts, set spending limits based on location, amount, merchant type or transaction type, and more.
Regularly Clear Your Browser History
Regularly clearing your browsing history helps protect your online security and reduces the risk of cyber threats. By removing stored data like visited websites, cookies, and cached files, you limit what hackers can learn about your online activity - keeping your personal information safer.

Common Types of Fraud
The best line of defense in preventing fraud is being able to detect it. Learn about the most common scams and how you can spot them.
What to do if you suspect fraud
- Notify your bank and credit card issuers immediately so they can close your accounts.
- Report the fraud to the Federal Trade Commission at ReportFraud.FTC.gov
- Contact the fraud unit of the three credit reporting agencies. Place a fraud alert on your credit report and consider placing a credit freeze so the criminal can’t open new accounts. The fraud unit numbers are:
- Equifax: (866) 349-5191
- Experian: (888) 397-3742
- TransUnion: (800) 680-7289
- File a police report.
- Make sure to maintain a log of all the contacts you make with authorities regarding the matter. Write down names, titles and phone numbers in case you need to contact them again or refer to them in future correspondence.
To learn more about fraud and identity theft prevention, visit the Federal Trade Commission's Scam Alerts page, or click below to view valuable resources on how to report, notify, mitigate, and dispute incidents of identity theft.
Don’t let scammers take over your online account!
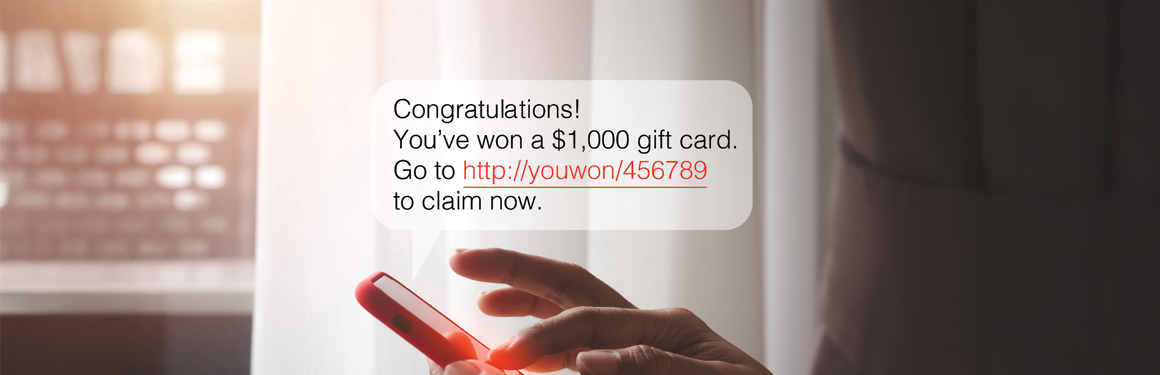
It can start with an Email Account Compromise (EAC) and could end with an Online Account Takeover (ATO). These two forms of cyber fraud are on the rise across the country. With both, criminals gain unauthorized access to your online banking accounts, or email often through stolen login credentials, phishing, or malware.
What is Account Takeover (ATO)?
Account takeover occurs when a scammer gains control of your online banking or other financial accounts. Once they have control, they may try to transfer your funds to their account, change contact information, apply for loans or credit using your information or order debit/credit cards.
What is Email Account Compromise (EAC)?
In EAC, criminals gain access to your personal or business email account. From there, they may monitor conversations for payment instructions. intercept or redirect money transfers (ACH, Wires, etc.), or impersonate you to defraud others (e.g., spoofing invoices).
How Do Fraudsters Accomplish These Attacks?
There are many ways scammers gain access to your accounts.
- Phishing emails that trick you into revealing passwords
- Spam emails that contain “Cancel” or “Unsubscribe” links that install malicious code on your device
- Scammer set up fake websites that show up when customers use search engines to find the bank website, rather than typing it directly into the browser.
- Weak or reused passwords across multiple sites
- Malware on devices used to access online accounts
- Public Wi-Fi interception or credential stuffing attacks
What Can You Do?
- Educate yourself about the risks. Stay informed about the latest fraud trends and tactics used by cybercriminals, including phishing scams, social engineering techniques, and other fraudulent activities.
- Use complex and unique passwords. Create strong, complex passwords for each of your online accounts. We recommend you change passwords for payment and bank apps periodically.
- Enable multi-factor authentication (MFA). Do not give out your MFA code (i.e., one time verification code)! Stockman will never ask for it. If someone is asking for that code, it means they have already successfully entered your username and password and are one step away from accessing your account. Never approve unrecognized login or transfer requests. Whenever possible, elect to use a Authenticator Application (Microsoft Authenticator, Google Authenticator, etc.) over text and email options.
- Implement dual control over payment activity. Enhance security by requiring two authorized individuals to complete a payment transaction.
- Regularly monitor account activity. Keep a close eye on your financial and online accounts for suspicious activity. Review your statements regularly and report any unauthorized transactions.
- Be wary of phishing attempts. Be cautious of unsolicited emails, messages, or phone calls requesting personal or financial information. Avoid clicking links or downloading attachments from unknown sources.
- Limit information shared on social media. Avoid posting sensitive personal information, which can be used to impersonate you or access your accounts.
- Keep software and devices updated. Ensure that your computer/phone/tablet’s operating system, web browsers, antivirus software, and other applications are up to date with the latest security patches and updates.
- Only access your online banking from the Official Bank Website (www.stockmanbank.com). Search engines can present imposter websites that have similar, but different, URL addresses made specifically to trick users to input their credentials into these fake sites .
- Use secure Wi-Fi networks. Avoid accessing sensitive accounts or conducting financial transactions over unsecured Wi-Fi networks and public hotspots. This includes hotels, Air B&B, coffee shops, airports, or any public Wi-Fi. If you must use these networks, install and activate a VPN on your device.
- Regularly update privacy settings. Review and update your privacy settings on social media and other online profiles to limit who can see your information and interactions.
In other words, be vigilant. If something doesn’t feel right call someone and trust your instincts. Be cautious when interacting online or sharing personal information. If something seems suspicious or too good to be true, it usually is!







